This tutorial covers the post installation basic configuration of Monowall (M0n0wall). This segment covers changing the default password, setting the time zone of the firewall. It also covers setting static IP address mappings via DHCP as well as configuring port forwarding. This is the second part in a series of tutorials which will range from basic configuration of the firewall to more advanced topics such as IPSEC tunnels and VPN clients.
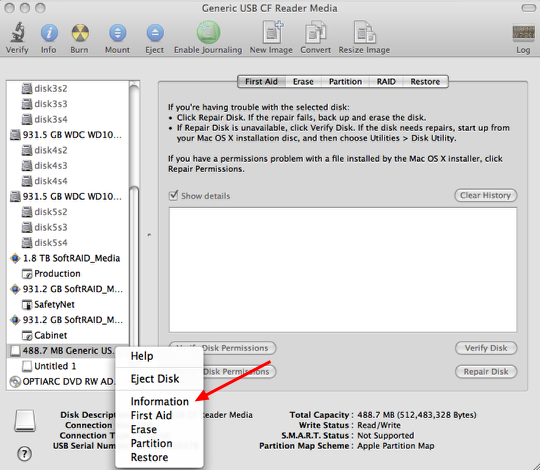
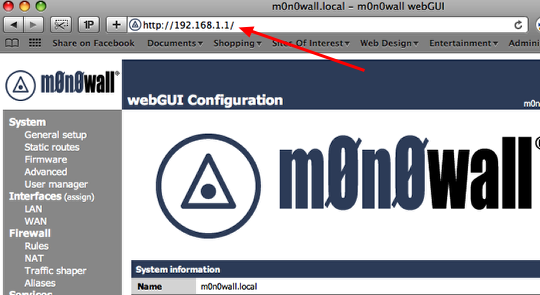
Log into the firewall

Change password & time zone
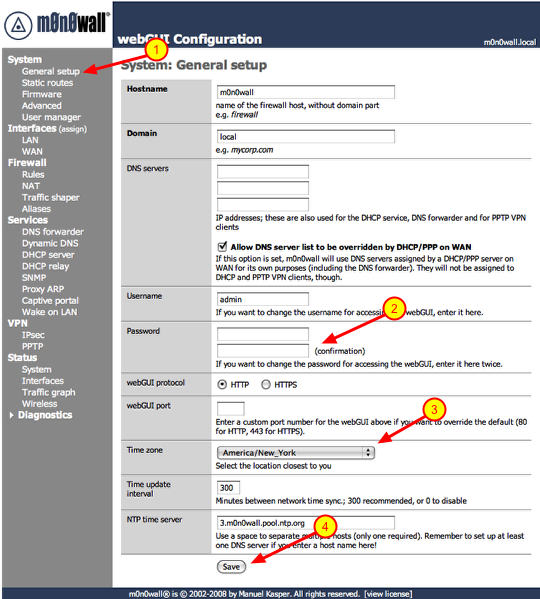
2.) Type in a new password in both boxes. As a general rule of thumb you should you upper and lowercase characters as well as symbols.
3.) Select the time zone you are in.
4.) Click the ‘Save’ button.
After you click save the firewall will prompt you to log back in with the new password.
Open the DHCP server configuration page
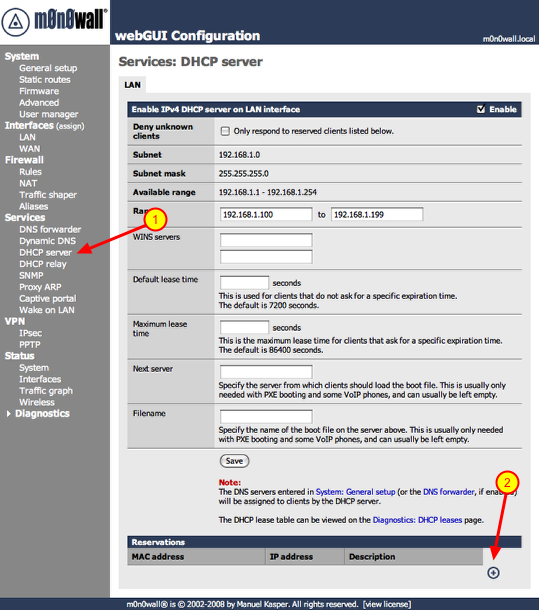
Also the static IPs have to be outside the range of IPs given out by the DHCP server. The default range is 100 – 199, keep that in mind.
1.) Click ‘DHCP server’ under the ‘Services’ section
2.) Click the ‘+’ symbol under the ‘Reservations’ section
Add static IP address mapping
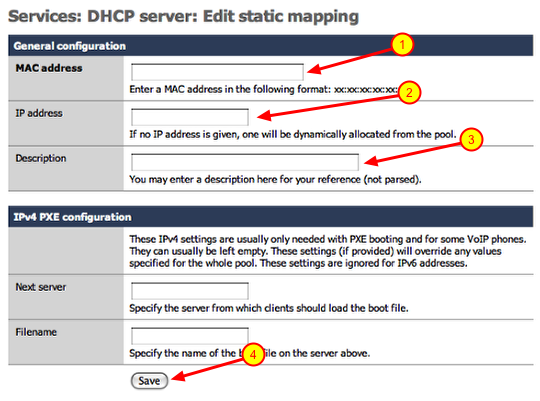
2.) Enter the IP address you would like to assign to the device. (i.e.. 192.168.1.200) Make sure the IP address falls within the range of your local network.
3.) Enter a description for the device you are adding a static mapping to and click save.
Repeat these steps for every device you need to add. Once you are done continue to the next section.
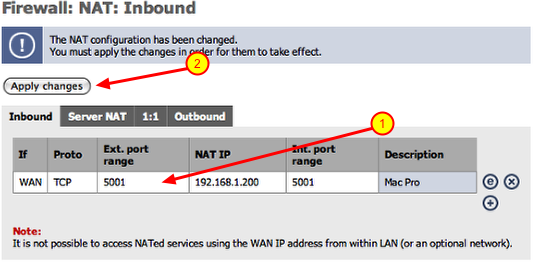
Apply changes, beware of the bugs though
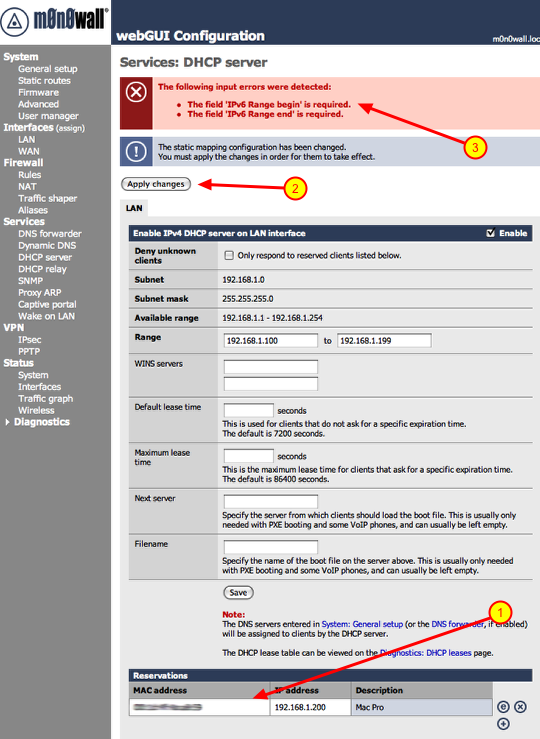
2.) Click the ‘Apply changes’ button.
3.) If you are installing 1.3 version you will see the above error. This is a bug in that version, it will be fixed in the next revision.
**If you do get this error after clicking ‘Apply changes’, you need to reboot the firewall. To do that click ‘Reboot system’ under the ‘Diagnostics’ section. Once you do that the changes will take affect.
Port forwarding
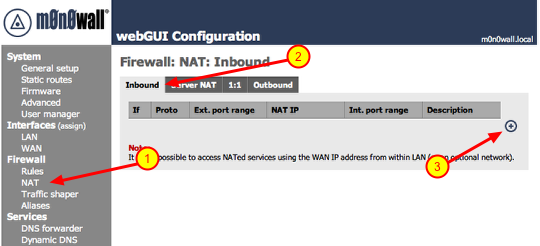
2.) Make sure ‘Inbound’ is selected
3.) Click the ‘+’ symbol
Adding port forwarding rule
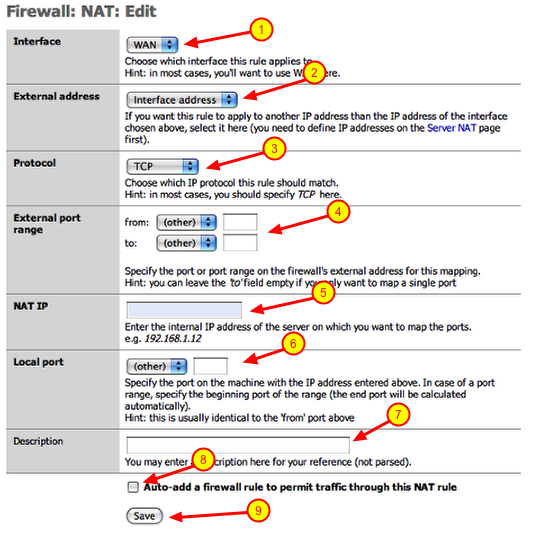
1.) Interface: should point to WAN
2.) External address: should point to ‘interface address’
3.) Protocol: select the appropriate protocol from the drop down (i.e.. TCP)
4.) External port range: enter the port number in both boxes (i.e.. 5001)
5.) NAT IP: this would be the IP address of the device on your local network (i.e.. 192.168.1.200)
6.) Local port: this would be the same port number used in step 4 (i.e.. 5001)
7.) Description: enter a thorough description of the device and port number you are forwarding for future reference
8.) Click the checkbox: This will automatically create the firewall rule you will need at the same time.
9.) Click the ‘Save’ button
Repeat these steps if you have multiple ports you have to open for a device. Also repeat these steps if you have multiple devices to add.
Apply changes
Ports for forwarding common devices
PS3: TCP 5223, UDP 3478. UDP 3479, UDP 3658 **Certain games may require additional port forward mappings, check with game vendor
SlingBox: TCP 5001
If you need information on ports for device not listed here, check with the manufacturers support web page. If you cannot find it there try Googling: firewall port forwarding for (then add your device and then hit the ‘Search’ button)